How to hack the Breakthrough Prize (ft. Session Confusion)
The Breakthrough Junior Challenge is an annual, global science video competition for high-school students. It’s run by Breakthrough Initiatives, the same organization that runs the Breakthrough Prize events.
In 2023, I discovered a critical vulnerability in the Breakthrough Challenge website. After over one year since it was patched, I am disclosing the bug for transparency. I believe this class of vulnerability, which I am introducing as ‘Session Confusion’, is often overlooked.
Set up #
While waiting for a video call related to an unrelated incident, I got bored and clicked around at my bookmarks. I rediscovered the Breakthrough Junior Challenge website that I submitted my entry to the year before.
The Breakthrough Challenge website allows participants to register accounts, which are used to submit personal details and video entries.
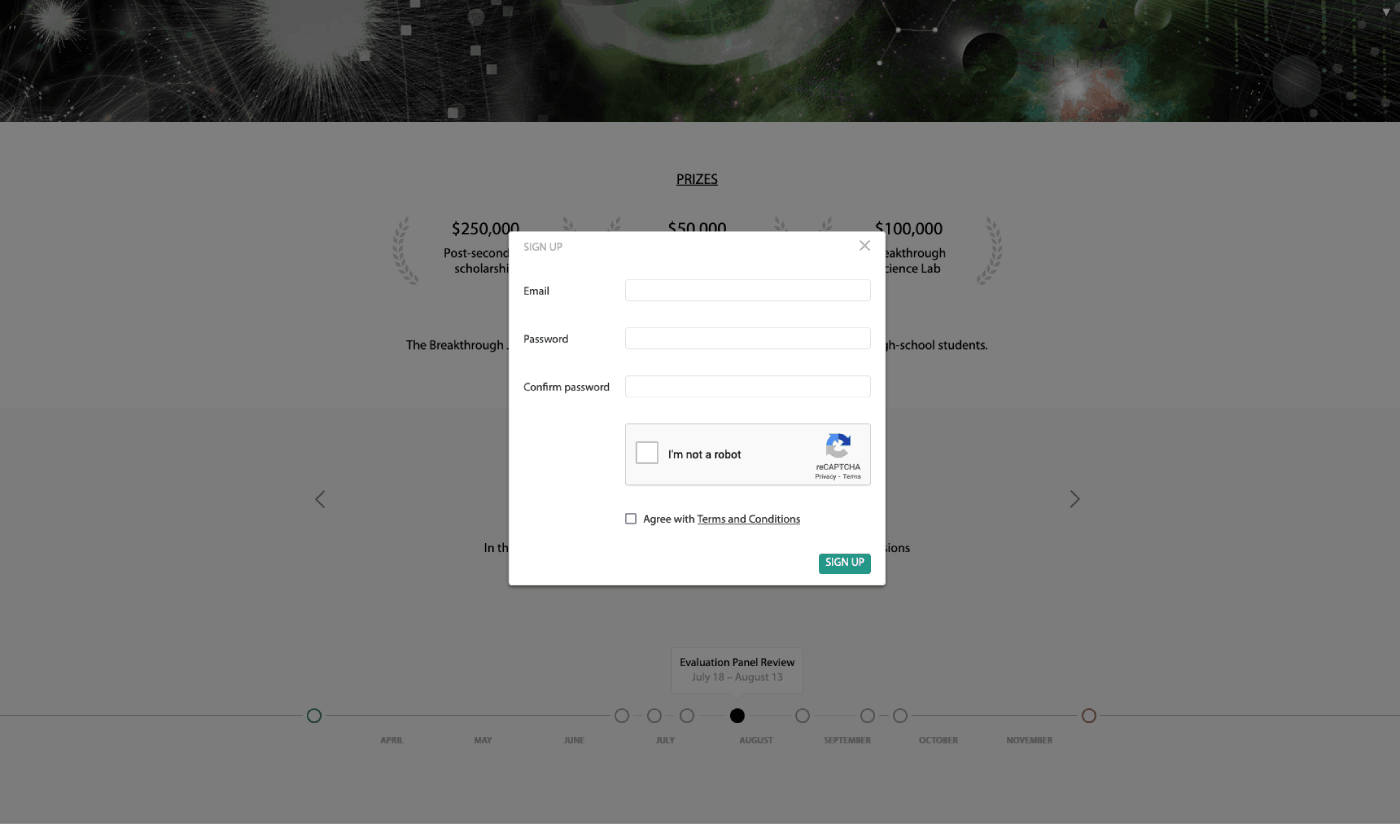
On a surface level, the website looks like it only exists for students.
But surely there has to be some kind of interface for the Breakthrough board to review videos, right?
Subdomains #
Subdomain enumeration is an extremely effective way to quickly discover the surface area of a web service. I found cp.breakthroughjuniorchallenge.org, which redirects to a login page.
Control… Panel…? #
This was a barebones login page - these are always fun, because it suggests whatever behind it is for internal use only.
Unsurprisingly, attempting to log in with my own account doesn’t work.
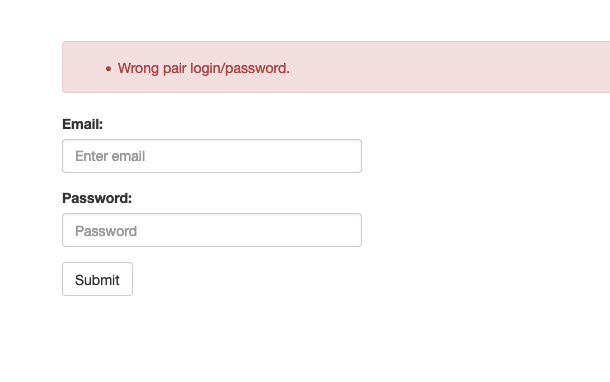
After trying different URLs, I quickly discovered that pages from breakthroughjuniorchallenge.org can be reached via cp.breakthroughjuniorchallenge.org, this suggests the applications are related in some way.
Session Confusion #
Exploring the cp.breakthroughjuniorchallenge.org domain further, I noticed that the login page’s structure mirrored the main site (minus styling). This raised a question: could the session management system be the same for both the public and internal sites?
To test this, I logged into my regular user account on breakthroughjuniorchallenge.org and captured the session cookie. Then, I tried to use the same laravel_session cookie on cp.breakthroughjuniorchallenge.org by simply changing the cookie’s domain scope to .breakthroughjuniorchallenge.org so it would be sent along on subdomains too.
Astonishingly, this worked. The internal control panel accepted my public session cookie, granting me access to administrative functions. This confirmed a serious vulnerability: the session tokens were not segregated between sites, leading to a case of “Session Confusion” (my own name).
It occurs in systems where session tokens, such as JWTs, are shared across multiple services without proper isolation. While the tokens themselves are signed and secure, the issue comes from the same session signing mechanism (the secret key) being used across both public-facing and administrative sites. This creates a security loophole, as a token issued for one context (e.g., a public site) can be accepted by another (e.g., an internal control panel), granting unintended access. In this case, the shared secret used to sign the session tokens allowed the internal site to mistakenly trust a session created for the public site, leading to unauthorized access to administrative functions.
Unauthorized Access #
Once inside the control panel, I found various administrative functionalities, including the ability to access user data, settings that alter the state of the competition and a directory of users. Fortunately, some of the interface was broken (relating to user management) - likely a side effect of my account not really existing on the admin site.
I would imagine that it would be possible to bypass the errors to make full use of the admin panel, but I did not want to access any sensitive data.
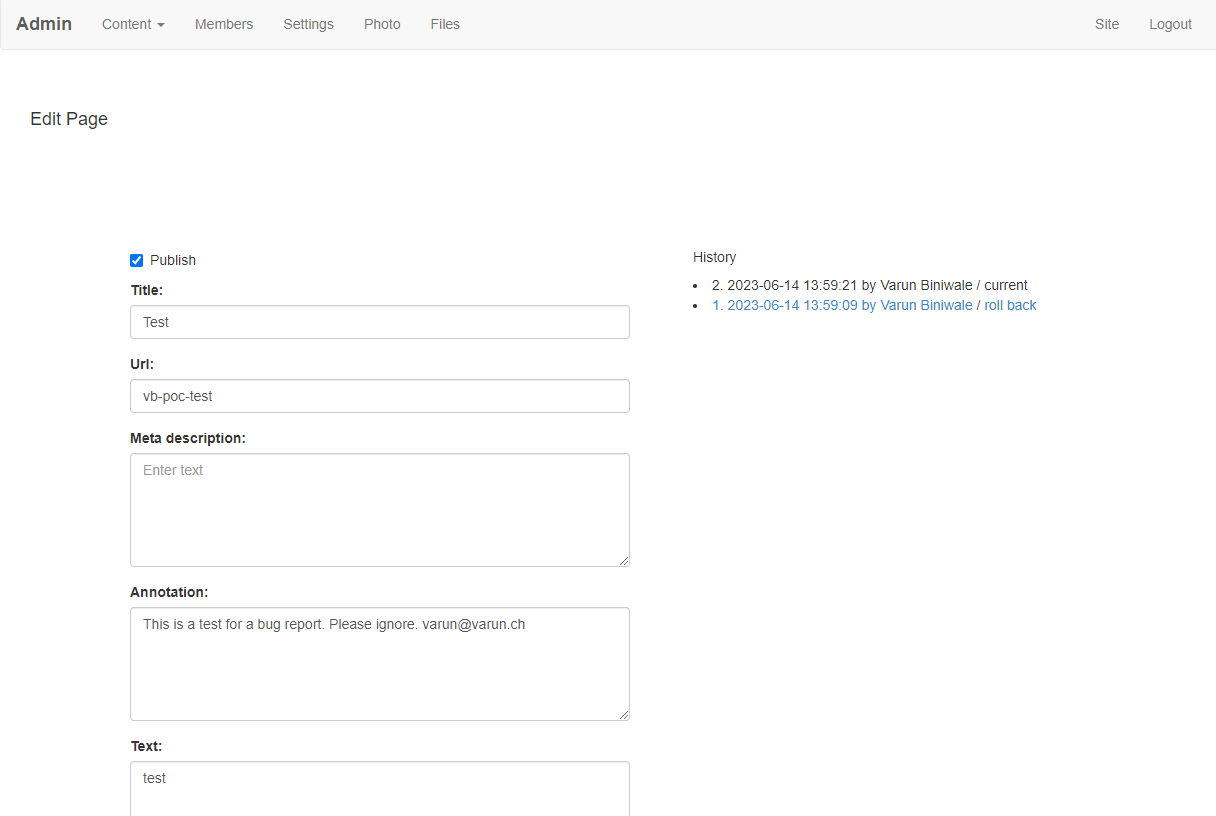
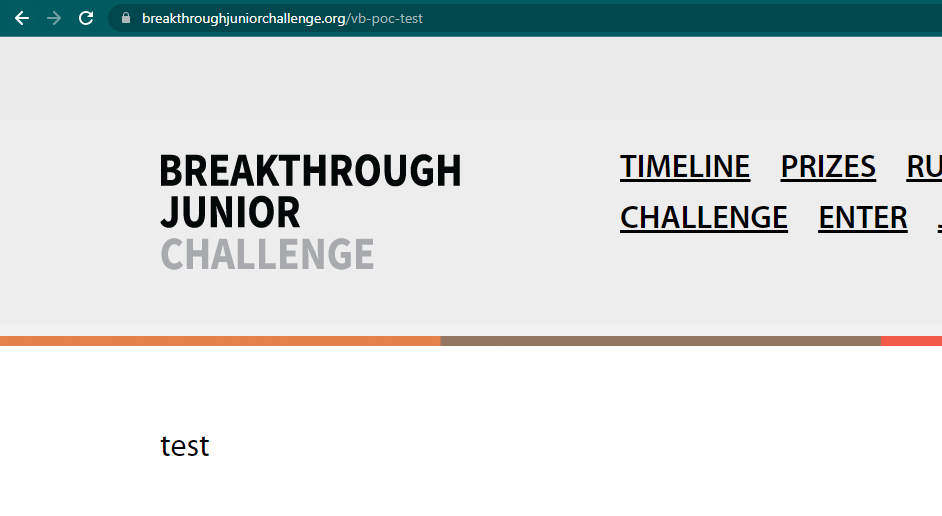
I tried to create a page on the root (expecting an error), but to my continued surprise, it went through and I had just edited the live running site. Oops.
Reporting #
I immediately undid any changes, logged out and reported this vulnerability via email detailing each step I took and the changes I made (just the creation and deletion of one page followed by invalidating my session).
Conclusion #
This bug would have allowed an unprivileged user to access some user data, modify competition state and vandalize the Breakthrough Junior Challenge website. The Breakthrough team responded extremely quickly, and the issue was fixed just 2 hours after I initially reported the vulnerability.
Timeline #
- 16:48 CET Jun 14, 2023: Email sent
- 18:55 CET Jun 14, 2023: Vulnerability acknowledged, “We believe we have fixed the problem.”
- 15:47 CET Jun 16, 2023: I acknowledge their reply, and confirm I can no longer reproduce the issue.
I asked on 12:34 CET Jun 24, 2023 and 12:36 CET Jun 23, 2024 about publishing this writeup. I did not receive a response. I am publishing this blog post today (with some details redacted) for transparency.